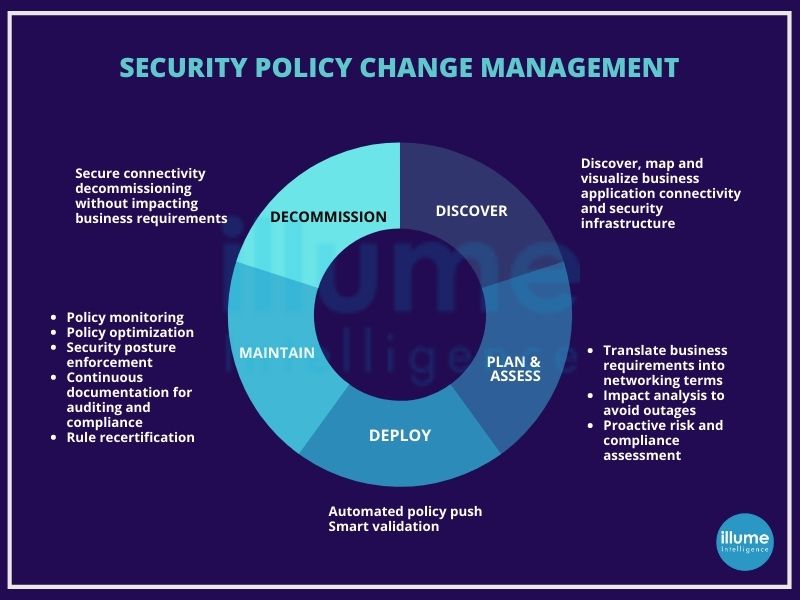
Latest Cyber Policy Changes: What You Should Know
In our increasingly digital world, keeping up with cyber policies is essential. These policies help protect us from online threats and ensure that our personal information remains safe. Recent changes in cyber policies have introduced new rules and guidelines that affect individuals and businesses alike. In this blog, we will explore the latest updates in cyber policies and what they mean for you.
New Data Privacy Regulations
Recent changes in data privacy regulations are designed to give individuals more control over their personal information. For example, the General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA) in the United States have set new standards for how companies handle your data. These regulations require businesses to be transparent about how they collect, use, and share your personal information.
Key Points:
- Consent: Companies must obtain your explicit consent before collecting or using your data.
- Access and Correction: You have the right to access your data and request corrections if it’s inaccurate.
- Data Portability: You can ask for a copy of your data in a format that you can transfer to another service provider.
These regulations aim to enhance your privacy and ensure that your personal information is used responsibly.
Stricter Cybersecurity Measures
To combat the rising number of cyber threats, new cybersecurity measures have been introduced. These measures focus on improving the security of systems and data. For instance, businesses are now required to implement advanced security protocols, such as multi-factor authentication (MFA) and encryption, to protect sensitive information.
Key Points:
- Multi-Factor Authentication (MFA): This adds an extra layer of security by requiring users to verify their identity through multiple methods, such as a password and a mobile code.
- Encryption: Encrypting data ensures that even if it is intercepted, it cannot be read without the decryption key.
- Incident Response Plans: Organizations must have a plan in place for responding to and recovering from cyberattacks.
These measures are crucial for protecting against unauthorized access and data breaches.
Enhanced Reporting Requirements
Another significant change is the enhancement of reporting requirements for cyber incidents. Businesses are now obligated to report certain types of cyberattacks to regulatory authorities within a specified timeframe. This helps in tracking cyber threats and ensuring that appropriate measures are taken to address them.
Key Points:
- Timely Reporting: Companies must report significant breaches within 72 hours of discovering them.
- Details Required: Reports should include details about the nature of the breach, the data affected, and the steps taken to mitigate the impact.
- Regulatory Oversight: Authorities will review reports to ensure compliance and address any potential risks.
Enhanced reporting helps in maintaining transparency and allows for quicker response to cyber threats.
Increased Focus on Supply Chain Security
Cybersecurity policies now place a greater emphasis on securing the supply chain. This means that businesses must ensure that their suppliers and partners also adhere to stringent cybersecurity practices. Supply chain attacks can compromise entire networks, making it essential for organizations to extend their security measures to third-party vendors.
Key Points:
- Vendor Assessments: Companies need to assess the security practices of their suppliers and partners.
- Contractual Obligations: Agreements with suppliers should include cybersecurity requirements.
- Monitoring: Ongoing monitoring of suppliers’ security practices is necessary to detect and address potential vulnerabilities.
By focusing on supply chain security, businesses can better protect themselves from potential threats introduced by third-party vendors.
Emphasis on Employee Training
Recent policy changes highlight the importance of employee training in cybersecurity. Employees are often the first line of defense against cyber threats, so educating them about security best practices is crucial. Training programs now focus on recognizing phishing attacks, handling sensitive data securely, and responding to security incidents.
Key Points:
- Phishing Awareness: Training helps employees recognize phishing emails and avoid falling victim to scams.
- Data Handling: Employees learn how to handle sensitive data securely and avoid common mistakes.
- Incident Reporting: Training ensures that employees know how to report suspicious activities or breaches.
Investing in employee training can significantly reduce the risk of cyber incidents and improve overall security posture.
Advancements in Cyber Insurance

Cyber insurance policies have also evolved in response to the increasing frequency and severity of cyberattacks. New policies now offer more comprehensive coverage and include provisions for various types of cyber incidents, such as data breaches and business interruption.
Key Points:
- Coverage Expansion: Policies now cover a broader range of cyber threats and incidents.
- Incident Response Services: Some policies include access to expert services for managing and mitigating cyber incidents.
- Compliance Requirements: Insurance providers may require businesses to meet certain cybersecurity standards to qualify for coverage.
Cyber insurance helps organizations manage the financial impact of cyber incidents and recover more effectively.
Global Cooperation on Cyber Threats
Finally, there is a growing emphasis on global cooperation to combat cyber threats. Countries and international organizations are working together to share information, develop joint strategies, and coordinate responses to cyberattacks. This collaborative approach helps in addressing cross-border cyber threats and improving overall global cybersecurity.
Key Points:
- Information Sharing: Countries share information about emerging threats and vulnerabilities.
- Joint Initiatives: International organizations coordinate efforts to develop cybersecurity standards and best practices.
- Incident Response Collaboration: In the event of a global cyberattack, countries work together to respond and mitigate the impact.
Global cooperation strengthens the ability to tackle cyber threats that transcend national borders.
Conclusion
Staying informed about the latest cyber policy changes is essential for protecting your personal and business data. By understanding new data privacy regulations, cybersecurity measures, reporting requirements, supply chain security, employee training, cyber insurance advancements, and global cooperation efforts, you can better navigate the evolving cyber landscape. Embracing these changes helps ensure that you and your organization remain resilient in the face of cyber threats.