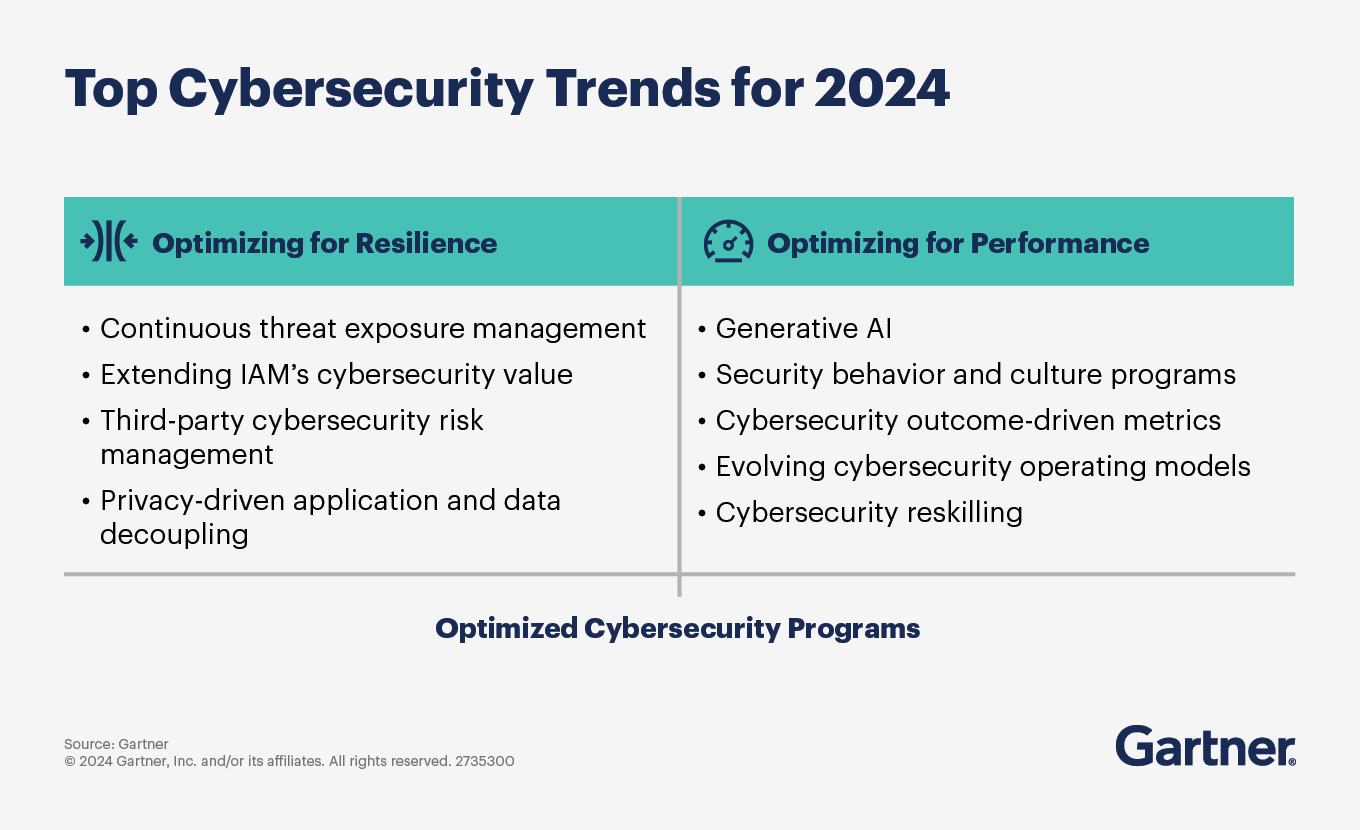
Cyber Security Investment Trends for 2024
Increasing Focus on AI and Machine Learning
In 2024, companies are investing more in artificial intelligence (AI) and machine learning (ML) to boost their cyber security. AI and ML help detect and respond to threats faster and more accurately. These technologies analyze vast amounts of data to identify patterns that might indicate a cyber attack. They can recognize unusual behavior, such as a sudden increase in login attempts or unexpected data transfers.
By using AI and ML, businesses can automate many security tasks that were previously done manually. For example, AI-powered systems can automatically block suspicious activities or notify security teams about potential threats. This reduces the burden on human security experts and speeds up the response to potential issues.
Moreover, AI and ML can predict future threats by analyzing trends and patterns from past attacks. This helps companies prepare for new types of cyber threats before they occur. Investing in AI and ML is becoming essential for businesses that want to stay ahead of increasingly sophisticated cyber threats.
Growth in Cloud Security Solutions
As more companies move their data and operations to the cloud, investing in cloud security solutions is becoming critical. Cloud environments offer flexibility and scalability, but they also come with unique security challenges. Cloud security solutions are designed to protect data stored online from unauthorized access and breaches.
These solutions include tools for encrypting data, managing user access, and monitoring network activity. They help ensure that sensitive information remains safe and only accessible to authorized users. Cloud security solutions also provide compliance with various regulations, which is important for companies operating in regulated industries.
Investing in cloud security is crucial for businesses that use cloud services for storing data or running applications. As cloud technology evolves, so do the security solutions designed to protect it. Companies are increasingly investing in advanced cloud security tools to safeguard their data and maintain trust with their customers.
Rise of Zero Trust Architecture
Zero Trust Architecture is gaining traction in 2024 as a key investment trend in cyber security. Unlike traditional security models that rely on perimeter defenses, Zero Trust operates on the principle of “never trust, always verify.” This means that no user or device is trusted by default, whether inside or outside the network.
In a Zero Trust model, every request for access is thoroughly checked before granting permission. This involves verifying the identity of the user or device and assessing the security posture of the device. Multi-factor authentication (MFA) and continuous monitoring are essential components of Zero Trust.
Investing in Zero Trust Architecture helps organizations protect their networks from internal and external threats. By enforcing strict access controls and continuously validating trust, businesses can minimize the risk of data breaches and unauthorized access. Zero Trust is becoming a crucial strategy for companies aiming to enhance their overall cyber security posture.
Emphasis on Threat Intelligence and Incident Response
In 2024, there is a strong focus on improving threat intelligence and incident response capabilities. Threat intelligence involves gathering and analyzing information about potential threats to identify and mitigate risks before they cause harm. This includes monitoring for new vulnerabilities, understanding emerging attack techniques, and sharing information with other organizations.
Incident response refers to the processes and tools used to handle security breaches or cyber attacks when they occur. Investing in robust incident response capabilities ensures that organizations can quickly detect, contain, and recover from security incidents. This includes having a well-defined incident response plan, conducting regular drills, and using advanced forensic tools to analyze and learn from incidents.
Effective threat intelligence and incident response are critical for minimizing the impact of cyber attacks and reducing recovery time. Companies are increasingly investing in these areas to strengthen their ability to prevent, detect, and respond to cyber threats effectively.
Growing Importance of Cyber Security Training and Awareness
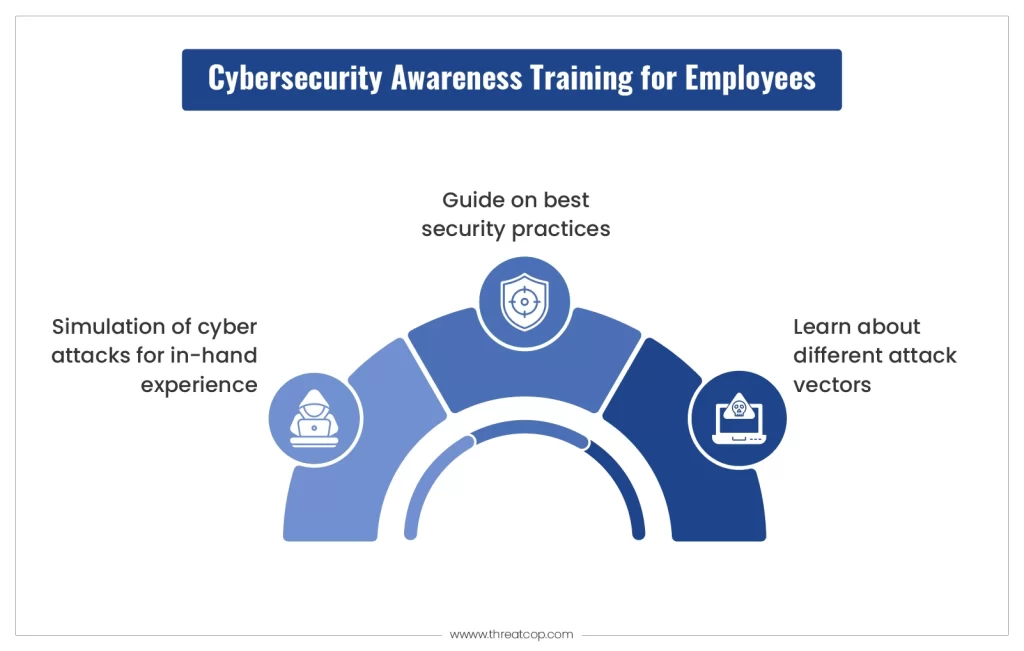
As cyber threats continue to evolve, investing in cyber security training and awareness is becoming increasingly important. Employees are often the first line of defense against cyber attacks, and their actions can significantly impact an organization’s security posture. Training programs help employees recognize phishing attempts, use strong passwords, and follow best practices for handling sensitive information.
Cyber security awareness programs also focus on creating a culture of security within the organization. This includes educating employees about the latest threats, promoting safe online behaviors, and encouraging reporting of suspicious activities. By investing in training and awareness, companies can reduce the risk of human error and enhance their overall security defenses.
In 2024, businesses are prioritizing cyber security training as a key component of their investment strategy. Ensuring that employees are well-informed and vigilant is essential for maintaining a strong defense against cyber threats.
Development of Next-Generation Firewalls and Intrusion Detection Systems
Next-generation firewalls (NGFWs) and intrusion detection systems (IDS) are gaining prominence as businesses invest in advanced security technologies. NGFWs go beyond traditional firewalls by incorporating features such as application awareness, user identity management, and advanced threat detection.
Intrusion detection systems (IDS) monitor network traffic for signs of suspicious or malicious activity. Modern IDS solutions use advanced algorithms and machine learning to detect anomalies that could indicate a potential breach. Combining NGFWs with IDS provides a comprehensive defense against a wide range of cyber threats.
Investing in next-generation firewalls and intrusion detection systems helps organizations enhance their network security and respond to threats more effectively. These technologies offer improved protection against sophisticated attacks and help ensure that network traffic is continuously monitored and secured.
Adoption of Cyber Security Automation and Orchestration
Cyber security automation and orchestration are becoming essential investments for companies aiming to streamline their security operations. Automation involves using technology to perform repetitive security tasks without human intervention, while orchestration refers to coordinating and integrating various security tools and processes.
Automating tasks such as threat detection, incident response, and log analysis can significantly improve efficiency and reduce the risk of human error. Orchestration ensures that different security systems work together seamlessly, providing a unified approach to managing and responding to cyber threats.
By investing in cyber security automation and orchestration, organizations can enhance their ability to detect and respond to threats quickly. These technologies help reduce the workload on security teams, improve the accuracy of threat detection, and enable more effective incident response.