Healthcare Cyber Attacks: Latest News and Alerts
Healthcare Cyber Attacks
Healthcare cyber attacks have become a significant concern as technology evolves. These attacks target medical institutions, such as hospitals and clinics, aiming to steal sensitive data, disrupt services, or demand ransom payments. With increasing reliance on digital records and online systems, healthcare providers are vulnerable to various forms of cyber threats. Understanding these threats and staying informed about the latest news and alerts can help protect both patients and healthcare systems.
Types of Healthcare Cyber Attacks
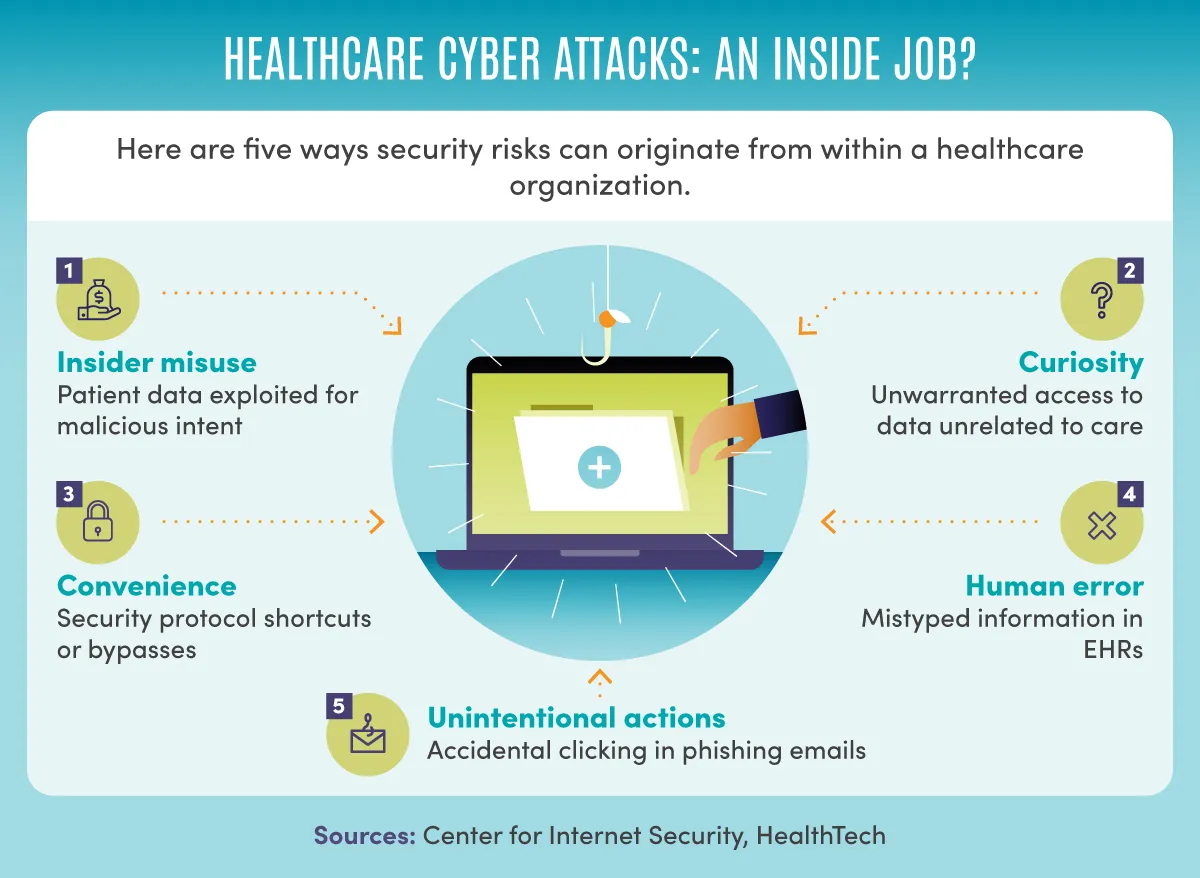
Healthcare cyber attacks come in various forms. One common type is ransomware attacks. In these attacks, hackers encrypt the healthcare provider’s data and demand a ransom for the decryption key. Another type is phishing attacks, where attackers use fake emails or messages to trick healthcare staff into revealing login credentials or other sensitive information. Data breaches are also frequent, where unauthorized individuals access and steal patient data. Each of these attacks can have serious consequences, including the disruption of medical services and exposure of private patient information.
Recent Trends in Healthcare Cyber Attacks
Recent trends show a rise in the sophistication and frequency of healthcare cyber attacks. Attackers are using advanced techniques, such as artificial intelligence, to breach systems more effectively. They also target specific vulnerabilities in outdated software or hardware. The COVID-19 pandemic has further increased risks, as many healthcare providers rapidly adopted new digital tools and remote work setups without adequate security measures. This situation has created more opportunities for cybercriminals to exploit weaknesses.
Notable Incidents and Breaches

Several notable healthcare cyber attacks have made headlines recently. For example, the attack on a major hospital chain in early 2024 led to the temporary closure of several facilities and disrupted patient care. Another incident involved a significant breach of a health insurance company, resulting in the exposure of millions of policyholders’ personal information. These high-profile cases highlight the severe impact of cyber attacks on healthcare systems and underscore the need for robust cybersecurity measures.
Current Alerts and Warnings
Staying updated with current alerts and warnings is crucial for mitigating the risk of healthcare cyber attacks. Government agencies and cybersecurity organizations regularly issue advisories about emerging threats and vulnerabilities. For instance, recent alerts have warned about new phishing campaigns targeting healthcare workers with fake COVID-19 vaccination information. It is essential for healthcare providers to monitor these alerts, implement recommended security measures, and train staff to recognize and respond to potential threats.
Preventative Measures and Best Practices
To protect against healthcare cyber attacks, implementing preventative measures is vital. First, healthcare providers should regularly update and patch their software and systems to address known vulnerabilities. Second, strong access controls, such as multi-factor authentication, should be in place to restrict unauthorized access. Third, conducting regular cybersecurity training for staff helps them recognize phishing attempts and other threats. Finally, having a robust incident response plan ensures that the organization can quickly address and recover from any cyber attack.
Conclusion
Healthcare cyber attacks pose a significant threat to medical institutions and patient privacy. By staying informed about the latest news and alerts, understanding the types of attacks, and implementing effective preventative measures, healthcare providers can better protect themselves against these threats. As technology continues to advance, ongoing vigilance and adaptation are essential in safeguarding healthcare systems from cyber criminals.