Nation-State Cyber Espionage: Latest Reports
Nation-State Cyber Espionage
Nation-state cyber espionage involves government-sponsored hacking to gather intelligence, disrupt other nations, or gain technological advantages. This type of cyber activity is usually sophisticated and well-funded. Unlike typical cybercrime, which aims for financial gain, nation-state espionage focuses on collecting sensitive information that can affect national security.
Governments employ cyber espionage to monitor rival nations, steal trade secrets, or influence political processes. They use various methods, including malware, phishing, and advanced persistent threats (APTs). These attacks are often hidden and can remain undetected for long periods.
Understanding the motives behind nation-state cyber espionage helps in recognizing the potential threats. Countries engage in cyber espionage to gain a competitive edge, strengthen their position in geopolitical conflicts, and protect their national interests. The latest reports indicate an increase in these activities, reflecting heightened global tensions.
The Rise of Advanced Persistent Threats (APTs)
Advanced Persistent Threats (APTs) are a significant concern in nation-state cyber espionage. An APT is a prolonged and targeted cyberattack where attackers gain unauthorized access to a network and remain there to steal information over time. Unlike standard cyberattacks, APTs are highly strategic and stealthy.
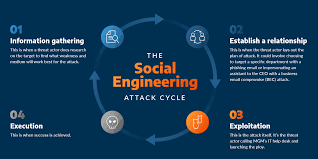
APTs often involve multiple stages. Initially, attackers use social engineering or exploit vulnerabilities to gain entry. Once inside, they move laterally within the network to identify and access valuable data. The final stage involves exfiltrating this data without triggering alarms.
Recent reports highlight that APTs are becoming more sophisticated. Attackers use advanced techniques to evade detection, such as employing encryption and anonymizing tools. They also target high-value targets like government agencies, defense contractors, and critical infrastructure. Understanding APTs helps organizations develop better security measures and respond effectively to these threats.
Notable Recent Incidents
Recent incidents of nation-state cyber espionage have made headlines, showcasing the evolving tactics and increasing risks. For instance, several high-profile attacks have been attributed to state-sponsored actors from various countries. These incidents often involve large-scale data breaches, which compromise sensitive information.
One notable incident involved a major attack on a government agency, where attackers accessed classified documents and communications. The breach was later linked to a nation-state actor aiming to gain political leverage and disrupt diplomatic relations. Another incident targeted a technology company, with attackers stealing intellectual property and trade secrets.
These incidents underscore the importance of vigilance and proactive cybersecurity measures. Organizations need to stay informed about the latest threats and invest in robust security protocols to protect their data and systems.
Global Responses and Countermeasures
In response to the growing threat of nation-state cyber espionage, governments and organizations worldwide are implementing various countermeasures. These responses include enhancing cybersecurity frameworks, increasing collaboration among nations, and developing new technologies to detect and prevent cyberattacks.
Governments are strengthening their cybersecurity policies and regulations, promoting information sharing among agencies and private sectors. They are also investing in advanced technologies, such as artificial intelligence and machine learning, to improve threat detection and response capabilities.
International cooperation is crucial in combating cyber espionage. Nations are working together to establish norms and agreements to address cyber threats and hold perpetrators accountable. The latest reports emphasize the need for a unified approach to tackle this global challenge and protect against the growing menace of nation-state cyber espionage.
The Future of Cyber Espionage
Looking ahead, the landscape of nation-state cyber espionage is expected to evolve further. As technology advances, so will the tactics used by state-sponsored actors. Emerging technologies, such as quantum computing and 5G networks, may introduce new vulnerabilities and challenges.
Organizations and governments must stay ahead of these developments by continuously updating their cybersecurity strategies and adopting innovative solutions. Preparing for future threats involves investing in research and development, enhancing collaboration, and fostering a culture of cybersecurity awareness.
The future of cyber espionage will likely see increased complexity and frequency of attacks. Staying informed about the latest trends and advancements in cybersecurity will be crucial in effectively defending against these evolving threats and ensuring a secure digital environment for all.
Innovations in Cyber Defense
In response to the growing threat of nation-state cyber espionage, innovations in cyber defense are continually evolving. These innovations include new technologies and strategies designed to enhance security and protect against sophisticated attacks.
One notable innovation is the use of artificial intelligence (AI) and machine learning (ML) to improve threat detection and response. AI-powered systems can analyze vast amounts of data to identify patterns and anomalies that may indicate a cyberattack. Similarly, ML algorithms can adapt and learn from new threats, enhancing the ability to detect and mitigate attacks in real-time.
Another advancement is the development of advanced encryption techniques to protect sensitive data. Encryption ensures that even if data is intercepted, it remains unreadable to unauthorized parties. Additionally, organizations are investing in threat intelligence platforms that provide real-time information about emerging threats and vulnerabilities.
These innovations in cyber defense are crucial for staying ahead of nation-state actors and safeguarding sensitive information. As cyber threats continue to evolve, ongoing research and development in cybersecurity technologies will play a vital role in maintaining robust defenses.
The Role of Cyber Diplomacy

Cyber diplomacy is becoming increasingly important in addressing the challenges of nation-state cyber espionage. It involves international efforts to establish norms, agreements, and collaborations to manage and mitigate cyber threats.
Countries are engaging in cyber diplomacy to create frameworks for responsible behavior in cyberspace and to promote cooperation in addressing cyber incidents. This includes negotiating treaties and agreements on cybersecurity, sharing information about threats and vulnerabilities, and coordinating responses to cyberattacks.
Cyber diplomacy also involves building partnerships between governments, private sectors, and international organizations. These partnerships facilitate the exchange of knowledge, resources, and best practices in cybersecurity. Through cyber diplomacy, nations can work together to strengthen global cyber resilience and address the complex challenges posed by nation-state cyber espionage.
Best Practices for Organizations
Organizations can adopt several best practices to defend against nation-state cyber espionage and protect their sensitive information. These practices include implementing strong security policies, investing in advanced technologies, and fostering a culture of cybersecurity awareness.
First, organizations should develop and enforce comprehensive cybersecurity policies that cover all aspects of their operations. This includes setting guidelines for data protection, access controls, and incident response. Regularly updating these policies to address new threats and vulnerabilities is also essential.
Investing in advanced cybersecurity technologies, such as firewalls, intrusion detection systems, and encryption tools, can help protect against sophisticated attacks. Additionally, organizations should conduct regular security audits and vulnerability assessments to identify and address potential weaknesses in their systems.
Fostering a culture of cybersecurity awareness among employees is also crucial. Training programs should educate staff about recognizing and responding to cyber threats, such as phishing scams and social engineering attacks. By promoting cybersecurity best practices, organizations can reduce the risk of falling victim to nation-state cyber espionage.
These best practices, when implemented effectively, can help organizations enhance their defenses and mitigate the risks associated with nation-state cyber espionage.